Kubernetes Credentials Management
In order to integrate a vendor-managed Kubernetes cluster into our system, you can either opt o Create a new cluster or Import an existing one. This process involves adding specific credentials based on your vendor.
Supported Credential Types include:
Visit https://home.appscode.com/user/settings/credentials to manage credential.
AWS
To create or import EKS clusters to AppsCode Dashboard, you need to create a access-key with the following policies.
- AmazonEC2FullAccess (AWS Managed Policy)
- AWSCloudFormationFullAccess (AWS Managed Policy)
- EKSAllAccess
- IamLimitedAccess
Steps:
- Create user
- Create required policies
- Attach the policies to the user
- Create access key
Details:
- Create usersh
aws iam create-user --user-name "eks-cluster" - Create policies
- Export AWS Account IDsh
export AWS_ACCOUNT_ID=$(aws sts get-caller-identity --query 'Account' --output text) - Create
AmazonEC2FullAccess (AWS Managed Policy)policyshecho '{ "Version": "2012-10-17", "Statement": [ { "Action": "ec2:*", "Effect": "Allow", "Resource": "*" }, { "Effect": "Allow", "Action": "elasticloadbalancing:*", "Resource": "*" }, { "Effect": "Allow", "Action": "cloudwatch:*", "Resource": "*" }, { "Effect": "Allow", "Action": "autoscaling:*", "Resource": "*" }, { "Effect": "Allow", "Action": "iam:CreateServiceLinkedRole", "Resource": "*", "Condition": { "StringEquals": { "iam:AWSServiceName": [ "autoscaling.amazonaws.com", "ec2scheduled.amazonaws.com", "elasticloadbalancing.amazonaws.com", "spot.amazonaws.com", "spotfleet.amazonaws.com", "transitgateway.amazonaws.com" ] } } } ] }' > ec2-policy.jsonshaws iam create-policy --policy-name ec2-policy --policy-document file://ec2-policy.json POLICY_ARN=$(aws iam list-policies --query 'Policies[?PolicyName==`ec2-policy`].Arn' --output text) aws iam attach-user-policy --user-name "eks-cluster" --policy-arn $POLICY_ARN - Create
AWSCloudFormationFullAccess (AWS Managed Policy)policyshecho '{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "cloudformation:*" ], "Resource": "*" } ] }' > cloudformation-policy.jsonshaws iam create-policy --policy-name cloudformation-policy --policy-document file://cloudformation-policy.json POLICY_ARN=$(aws iam list-policies --query 'Policies[?PolicyName==`cloudformation-policy`].Arn' --output text) aws iam attach-user-policy --user-name "eks-cluster" --policy-arn $POLICY_ARN - Create
EKSAllAccesspolicyshecho '{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "eks:*", "Resource": "*" }, { "Action": [ "ssm:GetParameter", "ssm:GetParameters" ], "Resource": [ "arn:aws:ssm:*:${AWS_ACCOUNT_ID}:parameter/aws/*", "arn:aws:ssm:*::parameter/aws/*" ], "Effect": "Allow" }, { "Action": [ "kms:CreateGrant", "kms:DescribeKey" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "logs:PutRetentionPolicy" ], "Resource": "*", "Effect": "Allow" } ] }' > eks-policy-template.json envsubst < eks-policy-template.json > eks-policy.jsonshaws iam create-policy --policy-name eks-policy --policy-document file://eks-policy.json POLICY_ARN=$(aws iam list-policies --query 'Policies[?PolicyName==`eks-policy`].Arn' --output text) aws iam attach-user-policy --user-name "eks-cluster" --policy-arn $POLICY_ARN - Create
IamLimitedAccesspolicyshecho '{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "iam:CreateInstanceProfile", "iam:DeleteInstanceProfile", "iam:GetInstanceProfile", "iam:RemoveRoleFromInstanceProfile", "iam:GetRole", "iam:CreateRole", "iam:DeleteRole", "iam:AttachRolePolicy", "iam:PutRolePolicy", "iam:AddRoleToInstanceProfile", "iam:ListInstanceProfilesForRole", "iam:PassRole", "iam:DetachRolePolicy", "iam:DeleteRolePolicy", "iam:GetRolePolicy", "iam:GetOpenIDConnectProvider", "iam:CreateOpenIDConnectProvider", "iam:DeleteOpenIDConnectProvider", "iam:TagOpenIDConnectProvider", "iam:ListAttachedRolePolicies", "iam:TagRole", "iam:GetPolicy", "iam:CreatePolicy", "iam:DeletePolicy", "iam:ListPolicyVersions" ], "Resource": [ "arn:aws:iam::${AWS_ACCOUNT_ID}:instance-profile/eksctl-*", "arn:aws:iam::${AWS_ACCOUNT_ID}:role/eksctl-*", "arn:aws:iam::${AWS_ACCOUNT_ID}:policy/eksctl-*", "arn:aws:iam::${AWS_ACCOUNT_ID}:oidc-provider/*", "arn:aws:iam::${AWS_ACCOUNT_ID}:role/aws-service-role/eks-nodegroup.amazonaws.com/AWSServiceRoleForAmazonEKSNodegroup", "arn:aws:iam::${AWS_ACCOUNT_ID}:role/eksctl-managed-*" ] }, { "Effect": "Allow", "Action": [ "iam:GetRole" ], "Resource": [ "arn:aws:iam::${AWS_ACCOUNT_ID}:role/*" ] }, { "Effect": "Allow", "Action": [ "iam:CreateServiceLinkedRole" ], "Resource": "*", "Condition": { "StringEquals": { "iam:AWSServiceName": [ "eks.amazonaws.com", "eks-nodegroup.amazonaws.com", "eks-fargate.amazonaws.com" ] } } } ] }' > iam-policy-template.json envsubst < iam-policy-template.json > iam-policy.jsonshaws iam create-policy --policy-name iam-policy --policy-document file://iam-policy.json POLICY_ARN=$(aws iam list-policies --query 'Policies[?PolicyName==`iam-policy`].Arn' --output text) aws iam attach-user-policy --user-name "eks-cluster" --policy-arn $POLICY_ARN
- Export AWS Account ID
- Create Access Token for the usersh
aws iam create-access-key --user-name "eks-cluster"
Then add the credential here you got from previous step.

Azure
To configure Azure credentials for accessing and managing Azure Kubernetes Service (AKS) clusters, follow these steps using the Azure CLI:
- Set the Azure subscription ID using the following command.sh
export AZURE_SUBSCRIPTION_ID=$(az account show --query id --output tsv) - Create Azure Service Principal with
Contributorrole.shaz ad sp create-for-rbac --role Contributor --scopes="/subscriptions/${AZURE_SUBSCRIPTION_ID}" --sdk-auth - Save Credentials
The command will output a JSON response containing the service principal details, including clientId (Application ID), clientSecret (Client Secret), subscriptionId, tenantId, and other information. Save these credentials securely as they will be used to configure the AKS cluster.
Then add the credential here.

Digital Ocean
To access Digital Ocean Managed clusters, you need to create a API token from Digital Ocean.
Ref: How to Create a Personal Access Token
Then add the credential here you got from Digital Ocean.
Google Cloud
To access GKE clusters, you need to create a GCP service account with with container.admin role.
- Set Project id, service account namesh
# Set the project ID where you registered your Domain PROJECT_ID="myproject-id" # change it to your project id GKE_SA_NAME="gke-cluster" # change it to your desired sa name GKE_SA_EMAIL="$GKE_SA_NAME@${PROJECT_ID}.iam.gserviceaccount.com" - Create Service account and Assign permissionsh
gcloud iam service-accounts create $GKE_SA_NAME --display-name $GKE_SA_NAME # assign google service account to dns.admin role in cloud-dns project gcloud projects add-iam-policy-binding $PROJECT_ID \ --member serviceAccount:$GKE_SA_EMAIL --role "roles/container.admin" - Create a Service Account Secretsh
# download static credentials gcloud iam service-accounts keys create $GKE_SA_NAME-credentials.json \ --iam-account $GKE_SA_EMAIL
Then add the service account credentials here.

Google OAuth
Simplest way to access GKE clusters is through creating Google OAuth type credential.
Just head over here and
- Choose a
Name - Select Credential Type:
Google OAuth - Click
Continue with Google
This will create a credential, you will be able to access your k8s cluster with.
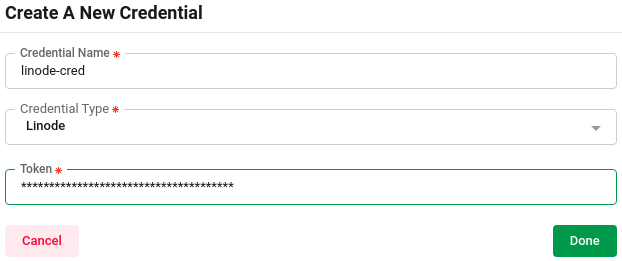
Linode
To access LKE clusters, you need to create a API token from Linode with the following permissions.
- Kubernetes (Read/Write)
Ref: Manage Linode Personal Access Tokens
Then add the credential here you got from Linode.
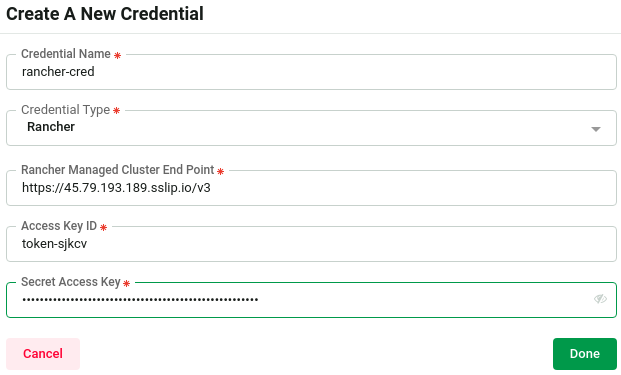
Rancher
To access Rancher clusters through AppsCode, you need to create an API token in your Rancher system. Follow these steps:
- In Rancher, click on the profile icon.
- Select
Account & API Keys. - Click
Create API Key. - Provide a name and set the expiration for the API key.
- Click
Createto complete the API token creation.
Reference: Rancher API Keys
Copy the generated access key, secret key, and API endpoint from the Account & API Keys overview page.
Next, add these credentials to the AppsCode user settings credentials page.



